An Insider Threat Program is establish to ensure safeguards and resources Insider threat incidents are possible in any sector or organization. An insider threat is typically a current or former employee, third-party contractor, or business partner.
Context
This case of study is for the course Cyber_Security_Pack
Mentor: Jeff Brown
This project were develop as a team and the members were:
- Manfred Segura Molina
- Luis Josué Chaves
- Breiner Monge
- Ronald Moreira Artavia
- Daniel Méndez
You can find this project in diferent presentations pdf Infographic
Case Study 3: Theft of Intellectual Property
A rogue nation sought to develop a next-generation trading platform for brokers and dealers. The rogue nation conspired to steal the technology (design and code) developed by the Costa Rica financial services company. A contractor (development manager) who had spent 15 years with that Costa Rica Company used a privileged position to help the rogue nation. The financial impact of this incident is estimated to be in the billions of dollars, and that does not factor in the consequent loss of competitive advantage for the firm.
Assumptions:
- The solution will require the team to think, develop and come up with recommendations for the case using related technologies.
- The financial institution has limited monetary and human resources to detect and mitigate this incident, they may rely heavily on the help that national and international police agencies could bring.
- Regulatory compliance and national laws could apply with this case
- Stakeholders will require a full overview of the case, with details regarding procedures and recommendations to solve the incident.
Other relevant details (background):
- The contractor has no access to any other proprietary information regarding external projects besides this one
- In order to win other business with the financial institution, another external vendor (a competitor for the current contractor - from which the person involved with the incident was hired) offered their services with a reduced cost to the financial institution, in order to help them to implement any recommendation that the group of advisors will deliver.
- Currently, the financial company has several technology providers with multiple layers of services, technical components, and heavily specialized personnel that will allow the financial institution to implement any recommendations that you will have regarding the case.
Why is important an Insider Threat Program
- Reduced costs of an insider attack. An insider threat program maximizes your chances to detect and deter an attack quickly, minimizing the damage an insider can cause.
- Compliance with standards, laws, and regulations. NIST Special Publication 800-53, NISPOM, the US National Insider Threat Policy, and Minimum Standards, and other IT standards and regulations oblige organizations to develop and maintain insider threat programs.
- Early detection of insider threats. Detecting insider threats is more challenging than detecting outside attacks. An insider threat program helps spot a threat before it becomes an attack and causes harm.
- Fast and efficient response to an insider attack. An insider threat program clearly outlines the procedures, tools, and personnel responsible for mitigating a threat. With this knowledge, employees can efficiently handle a cybersecurity incident.
- Encourage and incentivize correct behavior with training and awareness, policy and procedure, and management practices.
- Should also deter, detect, and prevent people from wrongdoing
- Mitigate the impact(s) of the insider act through appropriate management or enforcement actions
- Tailor their insider threat program and risk appetite to the organization’s unique mission, culture, critical assets, and threat landscape.
- Build a culture of reporting and prevention that establishes and reinforces a positive statement of an organization’s investment in the well-being of its people, as well as its overall resilience and operational effectiveness.
- Employ multi-disciplinary capabilities that are enabled by technologies and/or dedicated personnel based on the organization’s type, size, culture, nature, business value, and risk tolerance to acts of malicious, negligent, or unintentional insiders.
- Apply the framework of detecting and identify, assess, and manage for the prevention of, protection against, and mitigation of insider threats.
- Establish a protective and supportive culture, protect civil liberties, and maintain confidentiality.
- Assist organizations in providing a safe, non-threatening environment where individuals who might pose a threat are identified and helped before their actions can cause harm.
Key Components of an Insider Threat Program
- Principles and standards that align the program with the culture and business of an organization and describe its purpose, goals, and objectives.
- A prioritized list of critical assets, both physical and intellectual, that are essential to the operation or business of an organization and whose compromise, damage, or loss can have an adverse impact on its mission
- Definitions of the most significant and prevalent threats and how they could affect the organization’s critical assets
- Means to detect and identify indicators of potential risks
- An Incident Response Plan in case of an insider threat incident
- A committee of stakeholders for program governance and leadership
- An organizational culture that encourages and provides a means of reporting; where reporting potential threats, indicators, or concerns to a responsible party is a reasonable expectation and confidentiality is maintained
- A central information hub for the collection, integration, analysis, and storage of all elements pertaining to insider threats
- A threat management team for the assessment, response, and management of potential insider threats
What kind of activities could you do in an insider threat program?
- Identifies and focuses on those critical assets, data, and services that the organization defines as valuable
- Monitors behavior to detect and identify trusted insiders who breach the organization’s trust
- Assesses threats to determine the individual level of risk of identified persons of concern
- Manages the entire range of insider threats, including implementing strategies focused on the person of concern, potential victims, and/or parts of the organization vulnerable to or targeted by an insider threat
- Engages individual insiders who are potentially on the path to a hostile, negligent, or damaging act to deter, detect, and mitigate
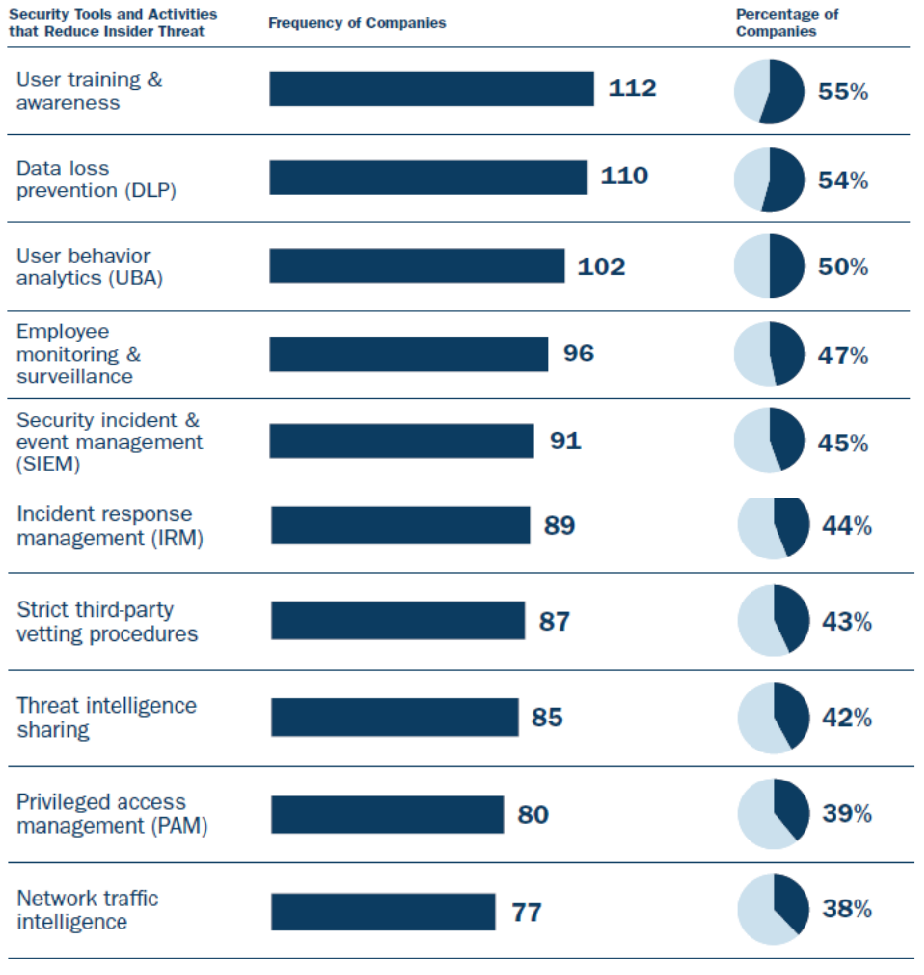
Frequently Used Tools and Activities to reduce the cyber threat
Seven Phases of an Insider Threat Program
1: Prioritize and Scope
This Insider Threat Program Plan applies to all staff of the company, contractor, products, services, facilities, information, equipment, networks, or systems
2: Orient
Operational risk: usually in terms of frauds, cyber threats, information leakages, service disruptions, or system processing errors. Security and Data Breach Risks Involving Personal Data The organization should be aware of potential security and data breach risks as well as issues that may arise from them Supply Chain Risk is associated with a lack of visibility into, understanding of, and control over many of the processes and decisions involved in the development and delivery of cyber products and services
3: Create a Current Profile
Organizational cybersecurity risk management practices are not formalized, and risk is managed in an ad hoc and sometimes reactive manner. Prioritization of cybersecurity activities may not be directly informed by organizational risk objectives, the threat environment, or business/mission requirements
4: Conduct a Risk Assessment
The risk might harm the Costa Rican financial services company and the people who use its services. Would be affected in terms of fraud, cyber threats, information leaks, service interruptions, or system processing errors. Currently, the financial company has several technology providers with multiple levels of services, technical components, and highly specialized personnel, who will evaluate the future recommendations that we will give in this audit.
5: Create a Target Profile
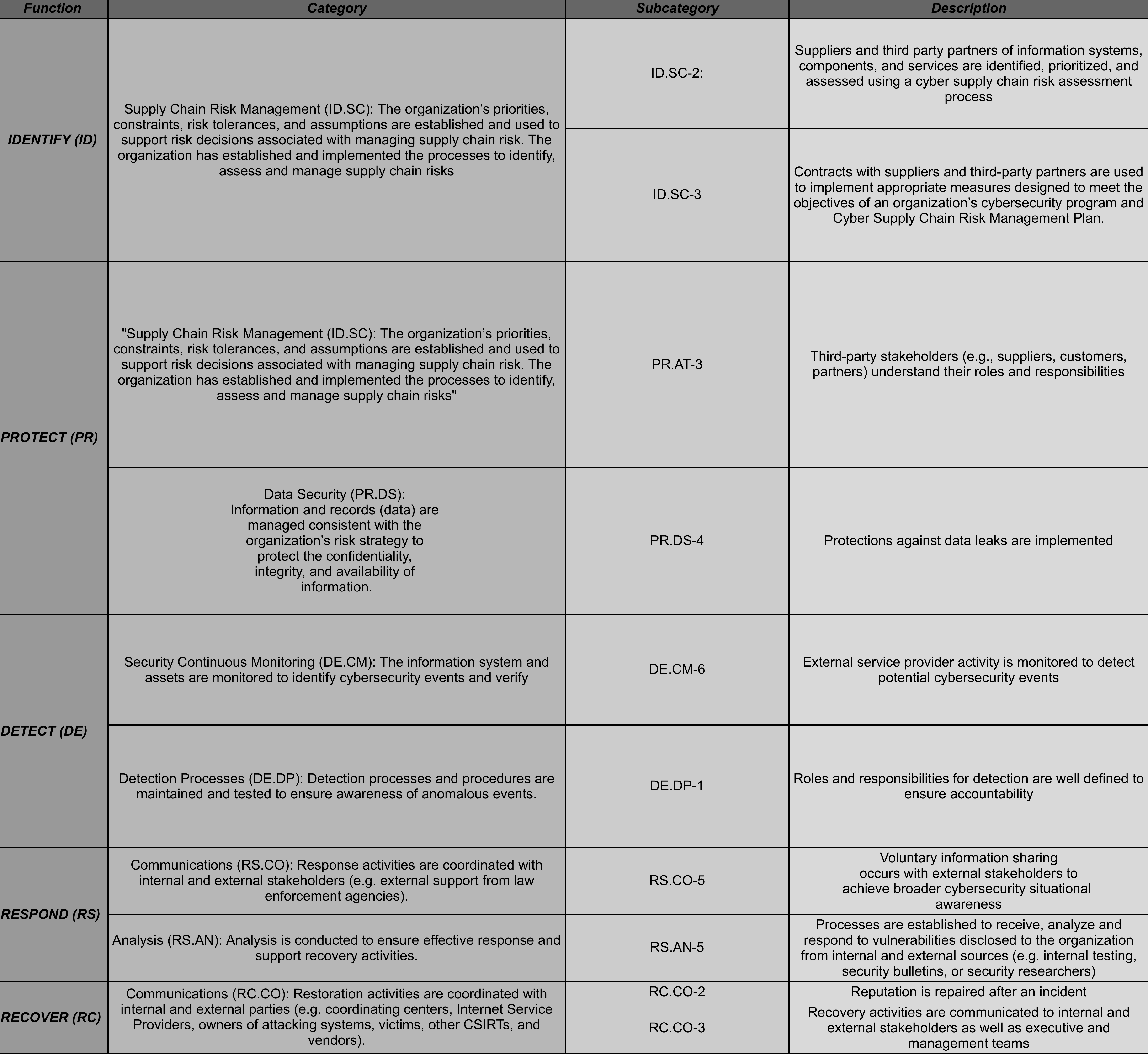
6: Determine, Analyze, and Prioritize Gaps
This Costa Rican financial services company is a neophyte in the development of cybersecurity measures but it is committed to advancing in the Framework Implementation Tiers. For them, it has several technology providers with multiple layers of services, technical components, and highly specialized personne
7: Implement Action Plan.
This company is committed to developing a culture of resilience, for the moment it will evaluate the Informative References indicated in the framework.
For example Vendors Management - APO10 (COBIT2019)
Which indicates:
- Identify and evaluate vendor relationships and contracts.
- Select vendors.
- Manage vendor relationships and contracts.
- Manage vendor risk.
- Monitor vendor performance and compliance.
The consulted files
- https://www.exabeam.com/ueba/insider-threats/
- https://prod.iq4.com/servlet/aws/NJ_College_-NIST.CSWP.04162018__22.pdf?r=1024/F/30599/1/ NJ_College_-NIST.CSWP.04162018__22.pdf&a=inline
- https://www.hkma.gov.hk/media/eng/doc/key-functions/banking-stability/supervisory-policy-manual /TM-E-1.pdf
- https://wiki.process-symphony.com.au/framework/lifecycle/process/vendors-management-apo10-c obit2019/